30 Recommended Ideas For Choosing A Cybersecurity Company in Dubai
30 Recommended Ideas For Choosing A Cybersecurity Company in Dubai
Blog Article
Top 10 Suggestions On How To Assess The Expertise And Credentials Of A Cyber Security Firm In Dubai.
1. Investigate Professional CertificationsStart your investigation by examining the professional certificates that are held by the employees of your company. Find credentials like copyright Security Professional (copyright), Certified Information Security Manager (CISM), Certified Ethical Hacker (CEH), and copyright Auditor (CISA). These certifications demonstrate an impressive level of knowledge and commitment to the highest standards of professional practice.
Review Team Experience
Ask what the background of the team is. Interview them about their experiences in the past, including the number of years they've worked in the field of cybersecurity as well as their previous roles. A team with diverse experiences in various sectors can provide a wider range of perspectives and solutions for cybersecurity problems.
3. Make sure you are aware of your educational background
Check the education level of key personnel. Achieving relevant qualifications in information technology, computer science, or cybersecurity may indicate a solid foundational knowledge of the subject. Credibility is enhanced when credentials from higher education are combined with professional certificates.
4. Analyzing specialization areas
Find out if there are any particularities among team members. If your business has specialized needs, then expertise in the areas of cloud, network, application, or data security may be advantageous. Particularized expertise will lead to better solutions for cybersecurity challenges.
5. For more information about ongoing training and development, click here.
Determine your company's commitment in advancing its training and development for employees. Cybersecurity is a constantly evolving field therefore it is crucial to stay up-to date with workshops, seminars, or other accreditations.
Review the past projects and case research
Find out about their past projects or case studies. You can learn more about their problem-solving abilities and their effectiveness by reading the detailed descriptions of the security challenges they've solved for their past clients.
7. Request testimonials from clients and references
Get testimonials and references from past clients to be a proof of the professionalism and efficiency of the business. Positive feedback from clients could be a sign of a solid reputation within the market and demonstrate the company's ability to deliver high-quality services.
8. Explore the role of industry in promoting
Find out how the company is involved in the cybersecurity community. Participation in industry conferences such as webinars, conferences, or contributions to cybersecurity-related publications could show a commitment to keeping up-to-date with the latest developments and the best practices.
9. Examine Research and Development efforts
Find out if the company invests in research and development (R&D) to expand the security offerings of its clients. Companies that focus on R&D are typically ahead of the curve in terms of developing new technologies and innovative solutions. They can supply clients with innovative cybersecurity approaches.
10. Find Awards and Recognition
Lastly, look into any awards or accolades won from the company in the cybersecurity sector. Awards within the field are an indication of dedication, quality and superior quality of customer service. They can boost the reputation and credibility of a company. Take a look at the top Cybersecurity Company in UAE for site tips including consulting security, cyber security what, digital security, best cyber security company, network security technologies, computer security services, network security management, it security technologies, ai in cybersecurity, cyber security information and more.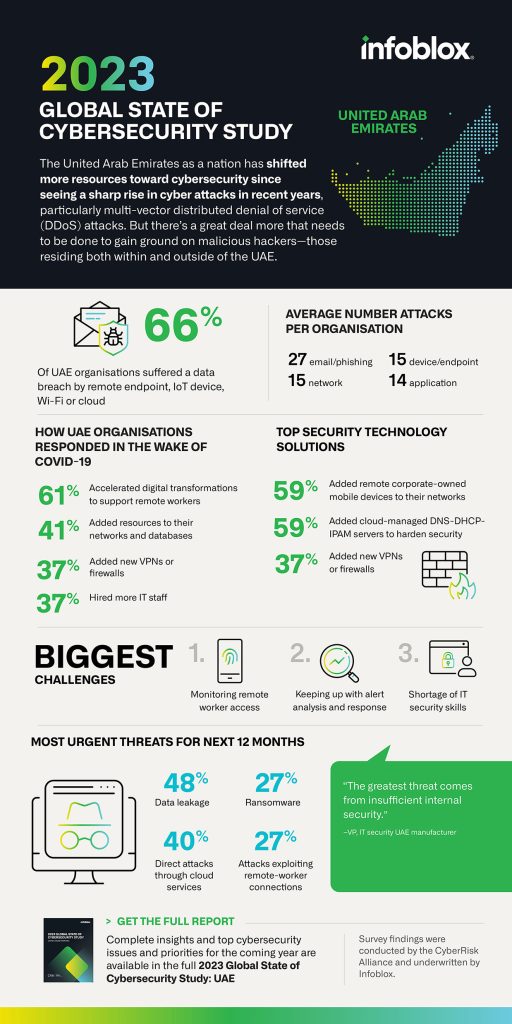
Top 10 Tips To Assess The Ability Of An Incident Response Team The Cybersecurity Service Company
1. Learn about Incident Response FrameworkBegin with an examination of the framework for responding to incidents that the company uses. A framework that is clearly defined, such as NIST Cybersecurity Framework (or the SANS Incident Response Process), indicates the company adheres to industry best practice for managing incidents. Make sure they have a clear and well-organized approach to dealing with incidents.
2. Evaluate Incident Response Team Expertise
Examine the qualifications and experiences of the participants. Look for certifications, such as Certified Incident Handlers or Certified Information Security Professionals. In order to effectively handle and reduce incidents, you need a knowledgeable team.
3. Review of Incident Responses to Past Incidents Case Studies
You can also request case studies or other examples from the firm of prior incidents they've handled. Examining the responses of real-world situations to incidents could provide insights into how efficient quick, efficient, and general the company's approach in managing incidents. Find out how they contained and resolved incidents by reading their detailed reports.
4. Check for 24/7 Incident response Accessibility
Check if the firm provides 24/7 incident response. Cybersecurity-related incidents can strike at any time. By having an available team around the clock, threats can be dealt with quickly. This reduces the risk of the damage and helps in recovering.
5. Request information about tools for detecting incidents
Examine the tools and technology that the company uses for incident detection and monitoring. The most effective detection tools, like Security Information and Event Management Systems (SIEM), and intrusion detection system (IDS), can help to identify threats earlier.
6. Examine Communication Protocols
Find out what protocols for communication are used by the business during an emergency. It is essential to establish clear and effective communication to coordinate response to the incident, communicate with stakeholders, and ensure that everyone knows their obligations. Learn how they can keep their customers updated throughout the entire procedure of responding.
7. Review Review Post-Incident Review Processes
Ask about the company's post-incident review processes. It is important to conduct thorough review after an incident to discover any lessons that can be taken away. Businesses that implement changes as a result of these reviews will be more efficient.
8. Evaluation of strategies for Remediation and Recovery
It is important to understand the tactics employed by an organization to recovering and remediation following an incident. Effective recovery plans should include how to restore data and systems as well as addressing weaknesses to prevent further incidents. Find out what approach they take in restoring and strengthening their systems following an incident.
9. Review compliance with regulatory Requirements
Ascertain that the company has emergency response capabilities that are in line with regulatory requirements. In certain industries, there are specific requirements regarding incident reporting and response. It is crucial to have a company who knows these regulations to be able to meet.
10. Seek out testimonials and references.
Finally, you can also seek references from current clients who used the service. Testimonials from clients can give an important insight into the efficiency as well as the reliability and satisfaction with the company's response during incidents. Follow the top rated penetration testing dubai for more info including network security, network security software, cyber security in usa, cybersec consulting, security technology, security ot, secure it company, managed security services provider, cybersecurity and business, cybersecurity firms and more.
Top 10 Tips To Evaluate The Tailored Solutions Provided By A Cybersecurity Services Company
1. Find out if you have the ability to customize your security by determining whether the business can customize their cybersecurity solution to meet the specific needs of your organization. Discuss their method of tailoring services based on your business's size, industry, and unique security threats. Your needs may not be satisfied with the "one-size-fits" approach.
2. Needs Analysis Method
Ask about the company's procedure for conducting a needs analysis. A thorough needs analysis should include understanding your current situation and identifying your weaknesses, and determining what you require. The more thorough their analysis is, the more they'll be able to match their solutions to your needs.
3. Review Previous Tailored Solutions
Case studies or examples which show how the business has tailored its offerings for past clients is a great idea. By studying these case studies, you can gain insights into the company’s ability to adapt its services to various conditions and its effectiveness when customizing approaches.
4. Knowing Industry Specific Solutions
Find out if the company offers solutions specific to your particular industry. Retail, healthcare, and financing all have their own cybersecurity issues. Customized solutions to address these particularities show the company's expertise and knowledge of the sector.
5. Evaluation of the Flexibility of Service Offerings
Assess the flexibility of your company in regards to changing the services they offer. Flexibility to adapt services as your business expands or as the threat landscape evolves is crucial for maintaining effective cybersecurity. You should ensure that the organization is prepared to make changes over time.
6. Check integration with existing systems
Ask the company if they can integrate their solutions to your existing IT infrastructure. Integration that is seamless is crucial to ensure that the new security measures function effectively without disrupting your current operations.
7. Make sure you have Custom Analytics and Reporting
It is also important to determine whether the business offers customized reports and analytics that are aligned with your objectives. Custom reports help you measure the effectiveness of cybersecurity measures and help you make informed decisions.
8. Assessment through collaboration
Check the company's desire to collaborate with your team. The company's willingness to collaborate closely with your team will determine the extent to which the solutions you get are effective and in line with your company's and operational processes. Choose companies that value communication and collaboration.
9. Consider the Scalability of Solutions.
Investigate whether the tailored solutions offered are scalable. When your business expands or evolves, your security requirements may change. Make sure that your company's security solutions are able to easily scale up or down to adapt to these changes without major changes.
10. Get feedback from clients on Tailored Service
Find feedback from clients about their experience with the custom solutions provided by your company. Testimonials can be a fantastic method to gain insight on how well the company can meet the needs of clients and how satisfied they are overall. Follow the best iconnect for website examples including basic cyber security, network security in cyber security, cyber cyber security, best cybersecurity firms, best cyber security company, cyber security information, cyber security what, cyber security projects, network security software, information security description and more.